Configuring WebSphere Security Propagation | ||
| ||
The first configuration runs two instances of WebSphere on the same physical computer. The second configuration uses the WebSphere Profile Wizard to create the second server, after the usual installation of the WebSphere Application Server. Each server is independent of the other, each with its own IP ports, JVM processes, and configuration. The wizard automatically creates the second server with nonconflicting IP ports for HTTP and RMI traffic.
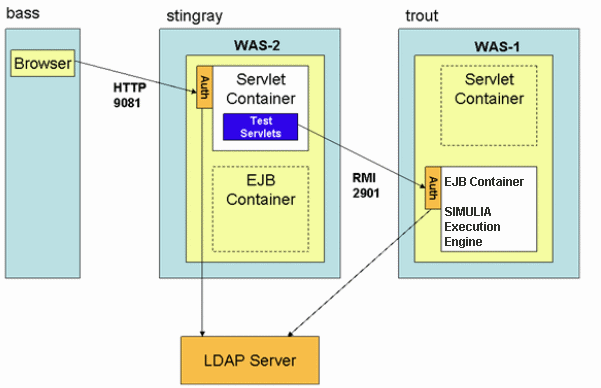
The following figures shows two instances of WebSphere on a single computer:
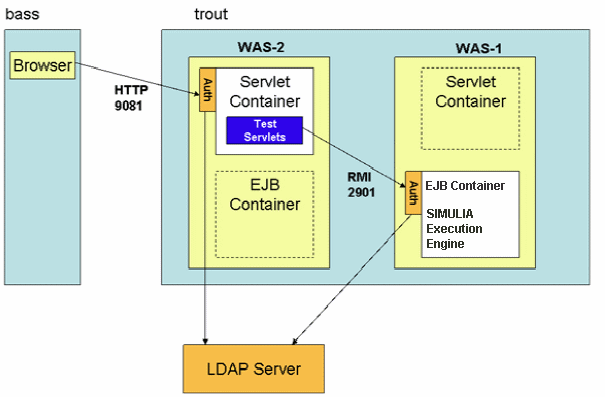
As shown, two instances (profiles) of WebSphere Application Server are deployed on a single computer. The WAS-1 server is configured with the usual port numbers (for example, 2901 for RMI) and has the usual SIMULIA Execution Engine deployment. The servlet container of this server is not used. The second instance (WAS-2) has the Web application deployed and is configured with port 9081 for HTTP. Both servers are running on host “trout,” have global security enabled, and are configured to connect to the same LDAP server. It is a requirement for this scenario that both servers are connected to the same LDAP server.
The browser connects to the HTTP server in the WAS-2 server. The container is configured to perform basic authentication on all Web resources, so the browser prompts the user for ID and password and authenticates the credentials with LDAP. Form-based authentication could also be used here, as well as an SSO system such as SiteMinder. Within the servlet container, a J2EE security context is established with the authenticated user identity.
When the servlet calls the SIMULIA Execution Engine EJBs in the WAS-1 server, it uses the standard RMI protocol. The two servers are configured so that the user identity and credentials are propagated to the WAS-1 server. The EJB call then executes in the security context of the user who originally logged on at the Web layer. From a SIMULIA Execution Engine EJB point of view, it appears the same as any call from an authenticated client. As a result, all the typical SIMULIA Execution Engine Access Control List processing can be completed.
The second server configuration is identical to the first except that the two WebSphere servers are installed on different physical computers. The logical architecture is the same.
The following figure shows two Instances of WebSphere on two computers: